Question 200
What was the most likely IPv4 address of we8105desk on 24AUG2016?
We have the name of the computer, and the time interval of interest so we can craft a query with this information.
index=botsv1 sourcetype=xmlwineventlog SourceIp=* SourceHostname="we8105desk.waynecorpinc.local" | table SourceIp| stats count by SourceIp

According to these results, the most likely IP address would be 192.168.250.100
Question 201
Amongst the Suricata signatures that detected the Cerber malware, which one alerted the fewest number of times? Submit ONLY the signature ID value as the answer.
index=botsv1 sourcetype=suricata event_type=alert cerber 192.168.250.100 | stats count by alert.signature alert.signature_id
The signature is 2816763: ETPRO TROJAN Ransomware/Cerber Checkin 2
Question 202
What fully qualified domain name (FQDN) does the Cerber ransomware attempt to direct the user to at the end of its encryption phase?
Using the IP of infected host, we can perform a query on the DNS logs excluding popular domains in order to narrow down suspicious domains requested.
index=botsv1 sourcetype=stream:dns src_ip=192.168.250.100 NOT (query IN ("*.arpa", "*.local", "*.microsoft.com")) | table dest_ip, _time, query | sort by _time desc
The domain requested is cerberhhyed5frqa.xmfir0.win
Question 203
What was the first suspicious domain visited by we8105desk on 24AUG2016?
Another suspicious domain is observed using the previous query : solidaritedeproximite.org
Question 204
During the initial Cerber infection a VB script is run. The entire script from this execution, pre-pended by the name of the launching .exe, can be found in a field in Splunk. What is the length of the value of this field?
index=botsv1 sourcetype=xmlwineventlog CommandLine="*.exe*.vbs*" "we8105desk.waynecorpinc.local" | sort _time desc | table CommandLine | eval cmd_len=len(CommandLine)
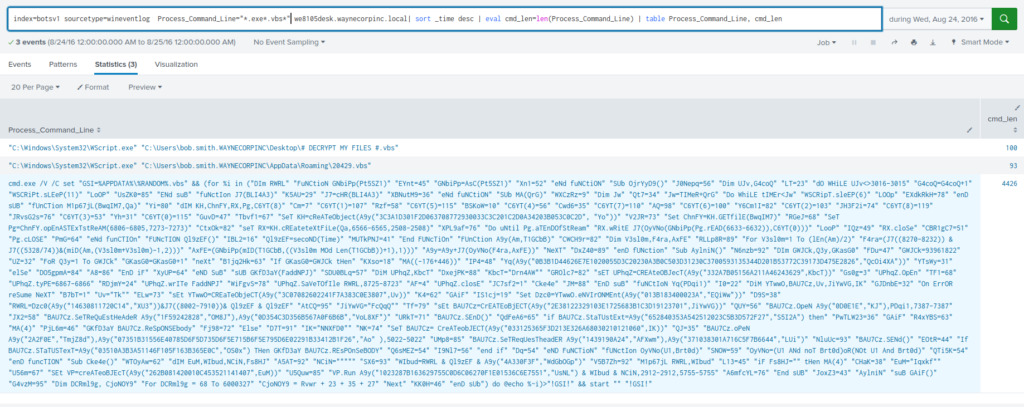
The command is 4490 characters long
Question 205
What is the name of the USB key inserted by Bob Smith?
Informations about USB keys are recorded in the registry
index=botsv1 sourcetype=winregistry host="we8105desk" USBSTOR
Question 206
Bob Smith’s workstation (we8105desk) was connected to a file server during the ransomware outbreak. What is the IPv4 address of the file server?
Hypothesis: The most common destination IP would be the IP of the SMB server
index=botsv1 sourcetype=stream:smb src_ip=192.168.250.100 |stats count by dest_ip| sort - count
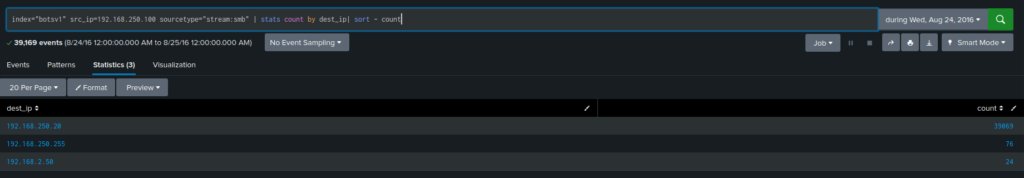
The IP address is 192.168.250.20
Question 207
How many distinct PDFs did the ransomware encrypt on the remote file server?
index=botsv1 we9041srv Relative_Target_Name=*.pdf sourcetype=wineventlog | dedup Relative_Target_Name |stats count by Relative_Target_Name|stats sum(count)
257 PDFs files have been envrypted on the remote file server.
Question 208
The VBscript found in question 204 launches 121214.tmp. What is the ParentProcessId of this initial launch?
index=botsv1 CommandLine=*121214.tmp* sourcetype=xmlwineventlog| sort _time desc| table CommandLine ParentProcessId
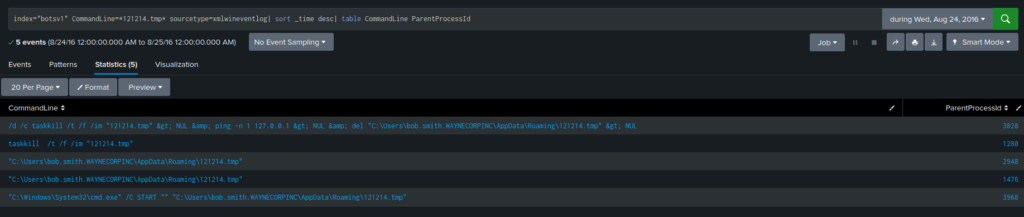
The ParentProcessId is 3968
Question 209
The Cerber ransomware encrypts files located in Bob Smith’s Windows profile. How many .txt files does it encrypt?
We can analyse the Sysmon logs for events related to the change of a file creation time by a process, namely Event ID 2
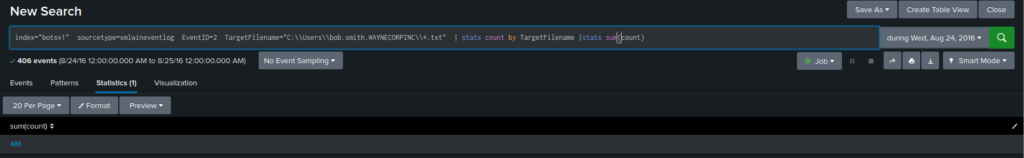
index=botsv1 sourcetype=xmlwineventlog TargetFilename="C:\\Users\\bob.smith.WAYNECORPINC\\*.txt" EventID=2| stats count by TargetFilename
406 txt files are encrypted by the Cerber ransomware.
Question 210
The malware downloads a file that contains the Cerber ransomware cryptor code. What is the name of that file?
We can go back and analyse the connection from the infected host to the malicious domain identified for the Cerber malware
index=botsv1 src_ip=192.168.250.100 uri=* solidaritedeproximite.org | table uri, http_method
The file downloaded is mhtr.jpg
Question 211
Now that you know the name of the ransomware’s encryptor file, what obfuscation technique does it likely use?
Given the name of the file, it was crafted in order to pass as an image file despite being an executable file. In that case, the obfuscation technique used is likely steganography.
